
PuMoC
A CTL Model Checker for Sequential Programs
Experiments on an extensive set of benchmarks are given below. The benchmarks are:
All the tests were run on a Fedora 13 with a 2.4GHz CPU and 2GB of memory.
1. Verifying Random Pushdown Systems.
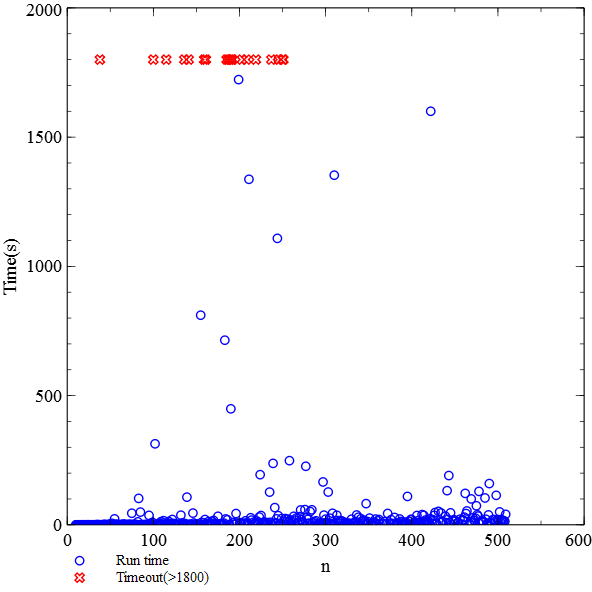
We randomly generated 500 PDSs each of them equipped with a random CTL formula. The number n of control locations and stack alphabet ranges from 10 to 510. The number of transition rules ranges from n2 to 2n2. The size of the CTL formulas ranges from 2 to 15. Figure (a) depicts the time consumption w.r.t. the size n. Only 5:2% (i.e., 26) of the cases run out of time (30 minutes) while the majority of cases terminated in a few seconds. Figure (b) depicts the memory consumption w.r.t. the size n. Only 6:6% (i.e., 33) of tests run out of memory with 2GB limitation. The majority of tests finished in a few MB. This benchmark includes 500 pushdown systems can be download [here].
 |
 |
| Figure (a): On Time Performance | Figure (b): On Memory Performance |
2. VerifyingWindows Drivers.
We tested 1461 versions of 30 real-world drivers. All these versions are taken from SLAM benchmarks. SLAM provides the boolean programs corresponding to these drivers.We checked 2 CTL formulas that are relevant for these drivers. The first formula r1 ensures that the programmer uses the API functions in the good order. This formula uses regular valuations to ensure that whenever a function named DeviceAdd is called, the function DeviceCreate will be called eventually before DeviceAdd returns. The second CTL formula r2 describes a locking property. Our results are described in Table 1. Column No. Versions gives the number of versions we considered of the corresponding driver. Column Avg. #LOC denotes the average size of the programs’ versions. Column Avg. Time(s) and Avg. Mem(MB) give the average time and memory in seconds and MB.
| Program | No. Versions | Avg. #LOC | r 1 | r 2 | ||
| Avg. Time(s) | Avg. Memory(Mb) | Avg. Time(s) | Avg. Memory(Mb) | |||
| 1394 | 10 |
7.9k | 48.8 | 30.45 | 27.82 | 9.8 |
| bluetooth | 37 |
10.32k | 67.83 | 34.38 | 28.11 | 10.43 |
| SD | 14 |
6.9k | 27.42 | 19.57 | 7.1 | 5.93 |
| PLX9x5x | 16 |
13.2k | 119.14 | 45.72 | 40.53 | 14.01 |
| amcc5933 | 14 |
10.0k | 54.5 | 32.26 | 16.84 | 9.4 |
| cancel | 69 |
3.4k | 20.95 | 12.43 | 4.01 | 4.34 |
| Echo | 68 |
5.4k | 28.34 | 19.1 | 7.46 | 5.66 |
| event | 20 |
4.8k | 32.04 | 18.24 | 7.22 | 5.35 |
| pcidrv | 72 |
29.1k | 422.58 | 115.56 | 181.52 | 36.58 |
| perfcounters | 16 |
2.2k | 11.84 | 8.58 | 2.57 | 2.82 |
| portio | 26 |
4.9k | 23.17 | 15.17 | 6 | 4.96 |
| registry | 35 |
11.4k | 150.85 | 46.36 | 56.83 | 14.91 |
| toaster_wdm_bus | 43 |
9.6k | 91.19 | 37.93 | 31.91 | 12.15 |
| toaster_wdm_func | 183 |
10.1k | 90.05 | 40.44 | 32.97 | 12.99 |
| toaster_wdm_toastmon | 41 |
4.5k | 32.15 | 17.58 | 8.24 | 5.7 |
| toaster_wdm_filter | 231 |
4.0k | 26.36 | 15.58 | 6.65 | 5.11 |
| toaster_kmdf | 165 |
5.0k | 19.45 | 15.13 | 5.19 | 4.89 |
| tracing | 62 |
2.8k | 15.9 | 10.54 | 3.64 | 3.54 |
| firefly | 17 |
4.2k | 12.96 | 10.21 | 3.14 | 3.45 |
| hidmapper | 29 |
2.5k | 13.65 | 9.33 | 2.71 | 3.14 |
| hidusbfx2 | 17 |
4.4k | 24.83 | 16.62 | 4.48 | 3.95 |
| HBtnKey | 34 |
5.5k | 48.06 | 21.76 | 13.29 | 6.98 |
| hiddigi | 65 |
9.2k | 84 | 35.46 | 28.9 | 11.25 |
| kbfiltr | 15 |
6.5k | 25.28 | 19.3 | 6.86 | 6.2 |
| moufiltr | 14 |
5.0k | 13.04 | 11.79 | 3.15 | 3.88 |
| vserial | 9 |
4.2k | 17.33 | 14.77 | 4.65 | 4.81 |
| smscir | 10 |
14.8k | 293.78 | 57.25 | 117.33 | 18.5 |
| network | 59 |
43.8k | 1283.84 | 171.42 | 594.93 | 52.95 |
| serial | 46 |
16.1k | 174.61 | 63.55 | 69.19 | 20.56 |
| storage | 84 |
57.3k | 923.24 | 224.42 | 401.03 | 69.38 |
Table 1. Model-Checking Drivers with PuMoC
3. Model checking C and Java Programs.
We also were able to check several CTL properties of several C and Java programs. We checked the C source code of a bounded model checker (verds). We also checked 4 real-world Java programs taken from JimpleToPDSolver, 4 real-world Java programs taken from a Java benchmark SciMark2 , and 7 real-world Java programs taken from JBDD . The experimental results are summarized in Table 2.
Program |
#LOC | Time(s) | Memory(MB) |
|
Java Program |
Namer |
60 |
0.03 |
0.62 |
cmdline |
3k |
5.72 |
32.14 |
|
readCmdLine |
78k |
525.32 |
149.62 |
|
usage |
95k |
3009.5 |
581.28 |
|
FFT |
1k |
11.33 |
8.74 |
|
Bench |
3k |
13.69 |
21.76 |
|
HTTPPost |
26k |
17.95 |
100.28 |
|
Applet |
159k |
4148.21 |
35.35 |
|
| Equivalence | 335 |
0.04 |
1.82 |
|
| Queens | 665 |
2.87 |
5.03 |
|
| Queens2 | 885 |
2.33 |
9.01 |
|
| Knight | 1k |
0.38 |
9.4 |
|
| DimacsSlover | 1k |
0.33 |
7.87 |
|
| interface | 1k |
23.86 |
26.17 |
|
| IQueens | 109k |
2440.32 |
411.67 |
|
| jlink | 37k |
2092.60 |
281.77 |
|
| JUnitTestRunner | 26k |
32.24 |
141.46 |
|
| DefanltDepDes | 28k |
1390.64 |
198.45 |
|
| IBiblioHelper | 89k |
4648.64 |
348.58 |
|
| EntryPoint | 11k |
20.14 |
66.39 |
|
| ProcessDestroyer | 11k |
128.22 |
87.06 |
|
| TestProcess | 1k |
0.19 |
5.89 |
|
| IvyAuthenticator | 3k |
40.81 |
27.91 |
|
| JunitTestRunnerTest | 28k |
1427.90 |
179.40 |
|
| Diagnostics | 59k |
1353.17 |
238.09 |
|
| DirectoryScanner | 17k |
626.41 |
113.68 |
|
| IntrospectionHelper | 5k |
3.92 |
36.03 |
|
| Launcher | 18k |
1341.98 |
185.55 |
|
| KeySubst | 3k |
7.40 |
15.60 |
|
| IPlanetEjbc | 22k |
703.68 |
175.50 |
|
| C Program | progreconstruct | 4k |
0.01 |
0.07 |
| cs2bool | 4k |
0.01 |
0.07 |
|
| specs | 4k |
0.01 |
0.08 |
|
| cnfsat | 4k |
0.01 |
0.07 |
|
| qmdwritecnf | 8k |
0.01 |
0.11 |
|
| treedopost | 8k |
128.22 |
87.06 |
|
| CNFspec2model | 8k |
0.19 |
5.89 |
|
| qmd2model | 8k |
40.81 |
27.91 |
|
Table 2. Checking C and Java programs with PuMoC
4. Data flow analysis of Java Programs.
PuMoC can also perform Data Flow Analysis of Java programs. Given a Java program, JimpletoPDSolver translates it into a PDS with def/use informations, where the atomic proposition de f (x) (resp. use(x)) of a variable x holds at a control point if its corresponding statement is an assignment (resp. a use) of the variable x. Using these informations, we can write CTL formulas that can solve some data flow analysis problems like reaching definitions, live variables, very busy expressions, and available expressions. For example the formula E[!de f (x)U use(x)] checks whether the variable x is used ithout being defined. This allows to do live variables analysis. Similarly, the formula AG(de f (x) => EF use(x)) states that whenever the variable x is defined, it should be used in some path. Checking such property allows to optimize programs. Indeed, the variable x does not need to be defined if x will not is used. Table 3 summarizes the results of our experiments. We made a comparision with PDSolver, a mu-calculus modelchecker for PDSs and Java programs (CTL formulas can be translated to mu-calculus). Our tool is more efficient.
Example |
#LOC | nu Y. ([]Y & (!def(x) | mu X. (<>X | use(x)))) |
AG(def(x)->EF use(x)) |
|
PDSolver |
PuMoC |
|||
Time(s) |
Time(s) | Memory(M) | ||
| RegisterTestAction | 3k | 5.14 | 0.71 |
5.23 |
| ELFDumpAction | 6k | 7.63 | 1.43 |
9.19 |
| ExampleFO2PDF | 17k | 108.4 | 10.33 |
24.12 |
| ExampleDOM2PDF | 18k | 54.53 | 11.92 |
29.21 |
| DisassembleAction | 54k | 458.77 | 134.18 |
87.09 |
| CFGAction | 90k | 1129.99 | 544.45 |
143.39 |
Example |
#LOC | nu Y. ([]Y & (!def(x) | mu X. (<>X | use(x)))) |
AG(def(x)->EF use(x)) |
|
PDSolver |
PuMoC |
|||
Time(s) |
Time(s) | Memory(M) | ||
| RegisterTestAction | 3k | 5.72 | 1.04 |
11.71 |
| ELFDumpAction | 6k | 76.59 | 12.10 |
28.83 |
| ExampleFO2PDF | 17k | 45.16 | 12.36 |
61.11 |
| ExampleDOM2PDF | 18k | 62.77 | 13.96 |
66.17 |
| DisassembleAction | 54k | >2000 | 138.19 |
150.48 |
| CFGAction | 90k | >2000 | 308.96 |
317.49 |
Table 3. Data flow analysis of Java Programs with PuMoC
Copyright © 2011-2012 LIAFA, University of Paris Diderot and CNRS.